Hacking, Security & Privacy News - Page 22
Samsung thinks SmartTV's are unsafe, makes security solution: GAIA
Samsung has just introduced a new three-layered approach to security for their SmartTV ecosystem to better secure any stored information, such as account details, payment details or any data being sent between it and the Internet.
This comes right after Samsung announced that they'd move more towards making their SmartTV's more of a hub for all of your IoT connected devices throughout your house. With that much data flowing between their TV's and being able to control your security system, lights and more, it's definitely a good idea to at least have a little encryption. Thankfully they're doing more than just a healthy dose of AES 256. Because of that centralized nature, security is important, Samsung said that "Protecting consumers' personal information is of the utmost importance to Samsung, both in terms of the company's values and what's needed for the continued growth and success of the IoT ecosystem."
GAIA works in three ways. First it separates the main operating system, the Tizen OS, from a secure space that can house all the important and personal bits of information and core services that's logically segmented in memory. This'll work in a similar way to how ARM's TrustZone and Intel's TXT works. The second piece is a built-in anti-malware service that can scan incoming and outgoing data, it'll also encrypt all traffic to and from the TV. The third part is much the same as the first, segmenting the OS in memory so that even if there is malware, it won't be able to touch the actual personal information.
Continue reading: Samsung thinks SmartTV's are unsafe, makes security solution: GAIA (full post)
AVG Chrome extension had a huge security hole, patched just in time
One of AVG's Chrome addons, Web TuneUP had a security hole that your could drive a tank into, something that could potentially let websites with malicious code in their CSS take control of your PC, though only in a trivial manner.
The exploit was originally found by Google, who reported it to AVG to have fixed. The initial fix wasn't quite good enough, so they just pushed out a new fix that seems to solve the issue. That being said, it still seems to be vulnerable to XSS attacks, though that should be fixed soon as well.
One generally thinks that antivirus companies are a bit more scrupulous and careful when designing their applications, but this mistake, and a mostly glaring one, calls to question the type of quality control and examination goes on before things go live. But it's best to fly without any addons, because all addons can potentially be security risks. Browse safe!
Continue reading: AVG Chrome extension had a huge security hole, patched just in time (full post)
Pre-installed malware on Raspberry Pi? They were asked to at least
It looks like some enterprising business people approached the Raspberry Pi Foundation with an odd business proposal, to pre-install their malware on the Raspberry Pi mini-computer.
In an email to the Foundation, a company, whose name was obviously redacted, was asking them to make available an exe file for installation (which wouldn't run on Linux anyway) in exchange for a sum of money for the amount of installations they detect.
This kind of tactic is surprising given the sheer audacity of asking a well-known organization, that prides itself on the many security applications of its minuscule box, outright to cheat its customers. It goes without saying that the Raspberry Pi Foundation didn't go along with their idea. It's even more hilarious that these peddlers of malware didn't seem to understand the platform being run on those devices. Maybe they'll ask Microsoft or Apple next?
Continue reading: Pre-installed malware on Raspberry Pi? They were asked to at least (full post)
The Hyatt hotels find malware hiding on their systems
The Hyatt chain of hotels just yesterday found malware running on their systems that operate the payment processing for their hotels.
In their statement they said that they've launched a full-scale investigation and are cooperating with some of the leading cyber-security experts in order to get the issues resolved. In the meantime, if you happen to have stayed at a Hyatt owned hotel within the past six months, be sure to keep an eye out on your bank accounts just in case something suspicious happens to show up.
How does one get malware onto a payment processing system? It's not terribly hard but there are best practices in place to make sure that it's difficult to do. Segmenting the network used and keeping it separate from other networks used for browsing the web, making sure that a proper IDS is in place to detect weird activity and limiting any IP addresses that actually access those systems processing card data to those on a whitelist. But those don't make it impossible, just harder and more likely to scare away all but the most seasoned and prepared of individuals. You can read all about the Payment Card Industry standards here.
Continue reading: The Hyatt hotels find malware hiding on their systems (full post)
Google is testing a new passwordless login system
In an effort to bolster account security, tech giant Google has confirmed that it's testing a new login system that doesn't require passwords.
Google is currently testing a new authentication method that could pave the way to password-free accounts in the near future. Google's method is very much like Yahoo's Account Key logins, which uses smartphone push notifications instead of manual passwords to log into Google accounts. The company's new sans password login method with a small batch of users, and one Reddit user has shared a few details on the new system.
According to an early access tester, the new method is pretty simple and is very much like linking a smartphone to a Roku to use a remote, or tethering a phone to an Xbox One to use Smartglass. Once your phone is linked and authorized to login to your Google account, the app sends a code that's shown on both screens, and users must type the same code to link the devices. Once that's done, users are logged in and can freely use their accounts. Basically Google's new method hinges on syncing, meaning you'll be matching digital pairs rather than typing in a per-session password.
Continue reading: Google is testing a new passwordless login system (full post)
Apple opposes Investigatory Powers Bill for hurting privacy, security
The UK government's Home Secretary Theresa May has proposed an Investigatory Powers Bill with the aim of bolstering intelligence agencies and law enforcement in surveillance. But, like the Patriot Act in America and Bill C-51 in Canada, it's being criticized for going too far.
Apple has joined the opposition in an effort to see the bill rewritten, saying in a rare public statement that it makes the "personal data of millions of law abiding citizens [...] less secure". Part of its issue is how vague the bill can be, thereby opening it up to abuse of current privacy rights, not just in the UK, but elsewhere, too.
The bill specifically affects Apple in that it may force them to remove the encryption featured in their iMessage and FaceTime apps, thereby allowing authorities to better spy on iPhone users as they see fit. It notes that while authorities may only be interested in select persons, once the public opens their private messages up, they're open to everyone.
Continue reading: Apple opposes Investigatory Powers Bill for hurting privacy, security (full post)
Infrastructure hacking isn't a new thing, New York dam lost in 2013
While we wrote that relatively small 'Western Nations' such as Australia are under possible infrastructure hacker threat due to low-security measures, news has come to light that a New York dam was infiltrated by Iranian hackers back in 2013.
With the dam being located no more than 20 miles from New York City, this Iranian hack likely came around thanks to Leon Panetta, ex-Defense Secretary, calling out Iran's hacking prowess in October 2012, putting Governments on high alert for possible hacker threats. With this hack taking place and being kept under the covers until recently, it's just one example of how infrastructure infiltration is a very real threat.
This classified dam is one of the very few public accounts of infrastructure control loss, with all major suppliers of electricity, sewage, water and more all linked to the internet.
Continue reading: Infrastructure hacking isn't a new thing, New York dam lost in 2013 (full post)
Juniper Networks VPN Firewall security breach probed by the FBI
Juniper Networks has had quite the week. On Thursday it seems that some unauthorized code was found to have been inserted into their ScreenOS, which forms the basis for their hardware filewalls. This malicious code would allow a backdoor into the firewall, letting potential attackers decrypt VPN traffic with the keys found inside.
The fun doesn't stop there, however. Now the FBI has now gotten involved and will be investigating the possibility of whether foreign governments had been involved with inserting the malicious code for the purposes of intercepting encrypted communications from government employees.
And even in the non-governmental sector, Juniper is a widely used brand of IT security products, so it can't be ruled out that it was a privately funded and conducted attack with motivations not tied to any government.
Continue reading: Juniper Networks VPN Firewall security breach probed by the FBI (full post)
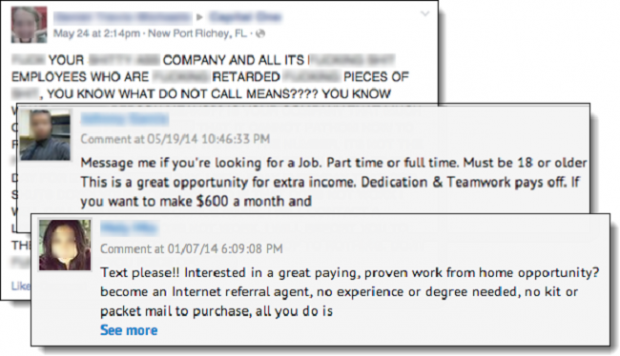
Security software removes spam bots on company Instagram promotions
We've all seen bots spamming phishing links on company social media promotions, trying to make use of the companies social networking promotion budget in order to lure in clicks from unsuspecting victims. Taclking the Instagram side of things is a company called Proofpoint, offering a cybersecurity service that aims to limit the exposure these phishing bots receive - named SocialPatrol.
With there being five million monthly active Instagram users in Australia alone and 400,000,000 'Instagrammers' across the globe, Proofpoint's aim is to ensure company promotions stay safe of hackers and retain legitimacy. Quite often when looking at promoted post on social media, customers will switch off when something is covered in "work from home!" or "buy cheap sunglasses here!" statements, sometimes cheapening the brand and possibly resulting in customers turning away.
In a recently issued press release, Global Customer Relations for General Mills Director, Jeff Hagen, spoke positively of this new technology, stating that it has "Helped us control high levels of spam and inappropriate comments on our Instagram accounts," adding "Without the Proofpoint SocialPatrol technology, our only recourse would have been costly expansion of our manual moderation or risk losing followers." While this will likely have little affect on the tech savvy audience TweakTown normally gathers, this technology should be a great invention for the elderly and youngster population alike, further helping protect them from threats online.
Continue reading: Security software removes spam bots on company Instagram promotions (full post)
PlayStation 4 jailbreak is here, confirms hacker on Twitter
A Twitter account with no profile photo and just over 2,000 followers called 'Cturt' has confirmed a Sony PlayStation 4 jailbreak success recently, telling the public that the "PS4 kernel exploit [is] finally working! Thanks to everyone involved!"
This jailbreak is said to enable a few interesting and helpful features, with CTurt explaining that this new breakthrough will enable users to "successfully dump RAM from other processes (like SceShellUI) using ptrace," further explaining that he will next be working on patching RAM.
While there is no posted guide, links or information as to how users can complete the same process on their consoles, there is a GitHub page of the same name, linked in the Twitter, where this information may surface in the near future. This news is exciting for developers looking at making custom firmware for the PlayStation 4, further opening up many other coding possibilities for community advancement of this device.
Continue reading: PlayStation 4 jailbreak is here, confirms hacker on Twitter (full post)