Hacking, Security & Privacy News - Page 12
Report: Chinese malware found pre-installed on US gov funded mobiles
The United States has a government initiative targeted at low-income Americans, and the premise of this initiative is to make it easier for low-income Americans to acquire a smartphone.
While that sounds like an amazing idea, and it is, what if those smartphones were found out to have pre-installed Chinese malware? Unfortunately, that seems to be the case as in October 2019, Malwarebytes started to receive complaints in its support system from users who were purchasing the most inexpensive smartphone that Assurance Wireless sells. Assurance Wireless, which is a federal Lifeline Assistance program under Virgin Mobile, is supported by the federal Universal Service Fund.
The most inexpensive smartphone they were selling was the Unimax (UMX) U686CL, and this was the phone that researchers picked up to test consumers' claims. It was discovered that the U686CL harbored malicious apps, such as an app called Wireless Update. The origin of this app can be traced back to Adups malware, which was created by a Chinese company that was caught gathering user data, creating backdoors users' phones, and auto-installing other malware.
Continue reading: Report: Chinese malware found pre-installed on US gov funded mobiles (full post)
'Project Artemis' is Microsoft's weapon against online child predators
Microsoft has announced a brand new online weapon that is designed to protect children from being groomed online by predators.
The new weapon is called "Project Artemis" and according to Mircosoft's blog post, is a new technique that can detect and report people who are suspected of child grooming. So how does it work? Project Artemis is a text-based review system that reviews conversations between people online and determines through a rating system whether or not its likely a party is grooming a child.
If a party is deemed likely to be grooming Artemis will then flag the conversation and notify a human moderator to come and check it for further evaluation. Project Artemis has been in development since November 2018, Microsoft hasn't been alone in the development either as The Meet Group, Roblox, Kik, Thorn and others have also given their assistance. Microsoft says in their post, "Project Artemis" is a significant step forward, but it is by no means a panacea". The fight for child safety online continues.
Continue reading: 'Project Artemis' is Microsoft's weapon against online child predators (full post)
Arlo has the first completely true wireless floodlight camera
CES 2020 - In this day and age, people are equipping their homes with cameras to help deter intruders. Most, if not all, of these cameras, require some form of wiring, but not Arlo's new camera.
Arlo has announced it's Arlo Pro 3 Floodlight Camera, a camera that is called the first truly wireless solution of its kind. The camera can be placed wherever it needs to go and has no connections, all users have to do is maintain the battery, and that's it.
The camera also has the capability of being able to record 2K + HDR support. It also has color night vision, an ambient light sensor that adjusts the brightness of the floodlight depending on surrounding light, and two-way audio if you really want to scare an intruder with your voice. The Arlo Pro 3 Floodlight Camera comes in at $250.
Continue reading: Arlo has the first completely true wireless floodlight camera (full post)
Facebook user data exposed online again, 267 million accounts now wild
A security researcher has reported that Facebook had more than 267 million users' sensitive information exposed online.
According to a report from Comparitech and a security researcher Bob Diachenko, more than 267 million Facebook users had their IDs, phone numbers and names exposed to the public online. This was discovered in a database that could be accessed without any means of a password or authentication, essentially being available to the public who would know how to access it.
Researchers believe this sensitive information was gathered as a part of an illegal scraping operation. According to Dianchenko, this data was exposed for nearly two weeks and was posted as a downloadable file in hacker forum. A Facebook spokesperson spoke to Engadget and said, "We are looking into this issue, but believe this is likely information obtained before changes we made in the past few years to better protect people's information".
Continue reading: Facebook user data exposed online again, 267 million accounts now wild (full post)
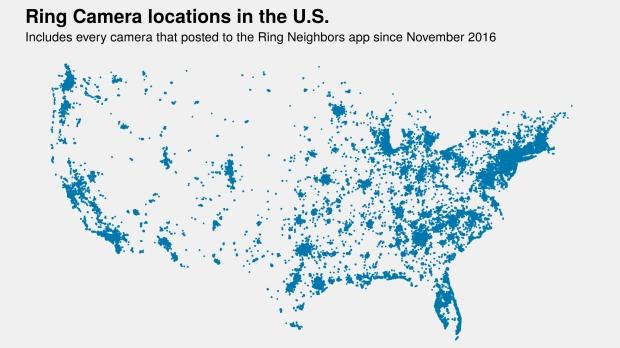
Amazon leaks out EVERY single home address of Ring camera customers
Amazon has just done something very, very naughty that might get them scrubbed off Santa's nice list -- the everything giant has just leaked out every single home address of its Ring surveillance camera customers.
In a new investigation by Gizmodo, it revealed that thousands of Amazon Ring camera customers have had their home addresses leaked. The exact location of their house has been displayed, with Gizmodo (and myself, and I'm sure anyone that reads this story) completely blown away. Gizmodo says its discovery casts "new doubt on the effectiveness of the company's privacy safeguards".
Gizmodo continued, adding that its discovery "further offers one of the most "striking" and "disturbing" glimpses yet, privacy experts said, of Amazon's privately run, omni-surveillance shroud that's enveloping U.S. cities".
Continue reading: Amazon leaks out EVERY single home address of Ring camera customers (full post)
USA has the most CCTV cameras per person than anywhere in the world
While China is usually labeled as a security state, it's been discovered that the USA has more CCTV camera's per person than anywhere in the world.
A new report was published by PreciseSecurity details, the number of closed-circuit TV (CCTV) cameras installed by each country. Each of these cameras has a purpose of monitoring what its viewing for security reasons, and if you expected China to have the most cameras you would of suspected right. PreciseSecurity says that China leads the world in CCTV cameras with 200 million installed.
The USA follows behind China with 50 million, then it drops down to Germany with 5.2, and then the United Kingdom with 5 million. What is most interesting, though, since China has such an overwhelming population, the USA actually holds 1st place for the 'highest number of CCTV cameras per person in the world' with 15.28 cameras per 100 people. China follows closely behind the US with 14.36 cameras per 100 people, and then the UK comes in with just 7.5 CCTV cameras per 100 people. For more information check out the report here.
Continue reading: USA has the most CCTV cameras per person than anywhere in the world (full post)
Black Friday smart TVs are a hackers portal to your home, FBI warns
The Black Friday sales just finished and just like every year a lot of people decided to pick up a new TV while they were heavily discounted. Now, the FBI has warned the public that the smart TV they just bought could possibly be hacked.
Since Black Friday has just finished, many participants in the sales would have grabbed a new snazzy TV for their family living room. While that is certainly a most-welcomed upgrade, it does come with a considerable potential downside. Since recently purchased TVs are smart TVs, they are designed to be connected to the internet for a means of accessing streaming platforms such as Netflix, Amazon Prime etc. Since they connected to the internet, that means they can be hacked.
A lot of the smart TVs being sold also have microphone and camera support, so if a hacker were somehow able to access your TV, they would be able to activate the TV's microphone and camera to listen in and watch you. FBI's Portland field office has warned of this very thing, saying that "Beyond the risk that your TV manufacturer and app developers may be listening and watching you, that television can also be a gateway for hackers to come into your home."
Continue reading: Black Friday smart TVs are a hackers portal to your home, FBI warns (full post)
Only in Japan: $1 hotel rooms offered if you livestream your stay 24/7
In another 'Only in Japan' post -- you can stay overnight in the Asahi Ryokan hotel for just $1 per night, but there's a big catch -- you'll need to livestream your stay 24/7.
Asahi Ryokan owner Tetsuya Inoue made the changes not long after taking on the business after his grandmother founded it, and tried to improve it for the new economy of 2019 and beyond. Asahi Ryokan is now offering guests rooms for just $1 per night if they agree to allowing their stay overnight (or longer) to be livestreamed.
There are rules and at least some privacy, with Asahi Ryokan not placing cameras in the bathroom, guests can turn the lights in the room on or off, and most importantly the livestream is video-only, so there's no audio to listen to that gives a thin layer of privacy. Inoue began running the hotel starting in 2018, explaining: "This is a very old ryokan and I was looking into a new business model. Our hotel is on the cheaper side, so we need some added value, something special that everyone will talk about".
Continue reading: Only in Japan: $1 hotel rooms offered if you livestream your stay 24/7 (full post)
1.2 billion people exposed in biggest data leak ever?!
In what has become one of the largest data leaks from a single source in history, the personal data of over 1.2 billion people has been exposed -- including names, email addresses, phone numbers, LinkedIn, Facebook, Twitter and more.
The leak was discovered by Bob Diachenko and Vinny Troia on October 16, 2019 in an open Elasticsearch server that had 4 billion user accounts inside of over 4TB of data. There were 1.2 billion unique people discovered inside of the leak, residing on an unprotected and totally-open Elasticsearch server with no password or any means of authentication protecting it -- so you could just download all 4TB of it easily.
The data in question comes from two brokerages, with California-based People Data Labs selling the data to advertisers who could use them for commercial purposes. User content to use this data commercially has not been approved, according to Troia. This particular data set has 622 million email addresses, 50 million unique phone numbers, and a bunch of different details from social media platforms.
Continue reading: 1.2 billion people exposed in biggest data leak ever?! (full post)
Report: voice fraud attacks have 350+% from 2014-2018 = 90 per minute
A cybersecurity company has released its annual Voice Intelligence Report, and their numbers are quite shocking.
According to Pindrop's annual Voice Intelligence Report, voice fraud continues to be a major threat for people as the report finds that between 2014 and 2018 fraud rates have climbed by 350%. The report also mentions the fraud rate for 2018, and it says, "The 2018 fraud rate is 1 in 685, remaining at the top of a five-year peak".
So, what type of voice fraud is occurring? The report mentions that insurance voice fraud has been the main target with widespread increases by 248%. The industries facing the highest fraud risks include insurance with 1 in 7,500 fraudulent calls, retail with 1 in 325 fraudulent calls, banking with 1 in 755 fraudulent calls, card issuers with 1 in 740 fraudulent calls, brokerages with 1 in 1,742 fraudulent calls, and credit unions with 1 in 1,339 fraudulent calls.
Continue reading: Report: voice fraud attacks have 350+% from 2014-2018 = 90 per minute (full post)