Microsoft has left an unpatched exploit in Windows 8 Consumer Preview. The exploit works on Windows 7, Windows Server 2008 R2 and Windows 8 Consumer Preview and has been documented and known for a while. The details of the exploit are pretty simple and can be done in under a minute if one is a fast typist.
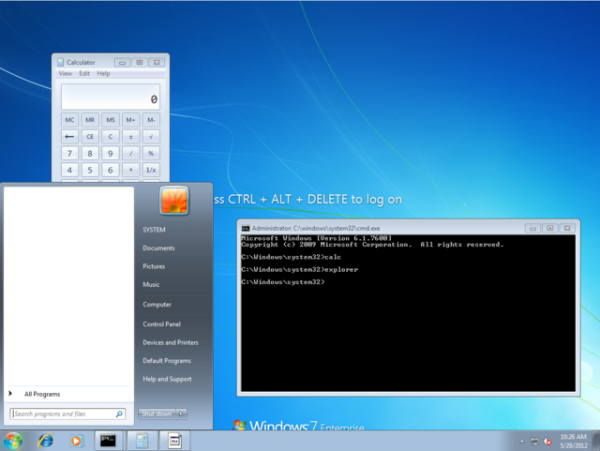
The general idea behind the exploit is to be able to run an elevated command prompt without even being logged in. It works by making a simple change in the registry so that when sticky keys is activated it launches the command prompt instead. The hack is virtually undetectable as all it is is a simple change in registry value.
To do the exploit one only needs to open command prompt once on the target PC and enter the code below. Once done, the hacker can return to the workstation at any point later in time and launch an administrator level command prompt just by pressing shift 5 times in a row. This could be of a serious nature for many different people, especially a business.
REG ADD "HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionssethc.exe" /v Debugger /t REG_SZ /d "C:windowssystem32cmd.exe"
Microsoft, at the time of writing, has yet to issue a statement regarding the exploit.

